Resource Public Key Infrastructure (RPKI) is a security framework by which network owners can validate and secure the critical route updates or Border Gateway Protocol (BGP) announcements between public Internet networks. BGP is essentially the central nervous system of the Internet and one of its fundamental building blocks.
The main function of BGP is to facilitate efficient routing between Autonomous Systems (AS), by building and maintaining the Internet routing table. The Internet routing table is effectively the navigation system of the Internet and without it, traffic would be unable to flow between its constituent networks. Unfortunately, routing equipment alone cannot distinguish between legitimate and malicious routing announcements, but network operators who implement RPKI validation and filtering can choose to reject announcements from networks not authorised to advertise those resources. In other words, RPKI is essentially a secure identification system for the BGP route information between autonomous systems.
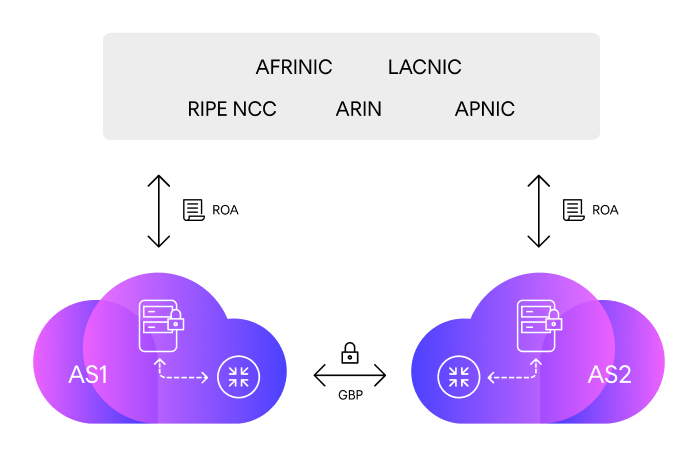
RPKI proves the association between specific IP address blocks or ASNs and the holders of those Internet number resources. In practical terms, validators are used within an AS to ensure the validity of BGP route updates. RPKI uses a certificate structure that verifies a resource holder's right of use of their resources and can be validated cryptographically. These certificates are known as Route Origin Authorization (ROA). ROA validation is an important process within the Resource Public Key Infrastructure (RPKI), since the certificates contain a number of critical routing parameters, including Origin ASN, Prefix and Max Length.
With RPKI, the certificate structure mirrors the way in which Internet number resources are distributed. That is, resources are initially distributed by IANA to the Regional Internet Registries (RIRs), who in turn distribute them to the Local Internet Registries (LIRs), and ultimately, to their customers – the autonomous system owners.
RPKI reduces the risk of accidental route leaks and helps mitigate the blast radius of any incidents caused either by human error or BGP optimization software. It also helps prevent malicious IP resource hijacks, which can result in critical outages or fraudulent traffic manipulation
Arelion was the first Tier-1 transit network in the world that launched the RPKI, successfully filtering invalid announcements from all external BGP sessions.
Our approach is that the industry would benefit from every single entity operating in the default-free zone deploying RPKI, so here are a couple of things to take into consideration:
RPKI is included in all Arelion’s IP Transit offers.
RPKI helps prevent accidental route leaks and malicious IP hijacks by cryptographically verifying the association between IP address blocks and their rightful owners, thereby ensuring only authorized networks can advertise specific routes.
Implementing RPKI allows network operators to enhance the security of the Internet routing table, protect against IP resource hijacking, and comply with security standards like MANRS, ultimately leading to a more secure and resilient Internet.
Serving customers in 129 countries, our 77,000 km fiber backbone spans North America, Europe and Asia. Our PoPs give you a direct route to the world’s best content and billions of end-users. Fiber-up control of our network with cutting-edge optical and IP technology deliver the scalability you need, whenever you need it.
